Imunify360 is the security solution for Linux web servers based on machine learning technology which utilizes a multi-layer approach to provide total protection against any types of malicious attacks or abnormal behaviour, including distributed brute force attacks.
Imunify360 provides:
- Advanced firewall with cloud heuristics and artificial intelligence for detecting new threats and protecting all servers that run the software - Capable of defending against brute force attacks, DoS attacks, and port scans.
- Intrusion Detection and Protection System - Comprehensive collection of “deny” policy rules for blocking all known attacks.
- Malware Scanning - Automatic scanning file systems for malware injection and cleaning up infected files.
- Patch Management - rebootless Secure Kernel powered by KernelCare keeps the server secure by automatically patching kernels without rebooting the server.
- Website Reputation Monitoring - Analyzing if a website or IPs are blocked by any blacklists and notifying if they are.
- Proactive Defense - Proactive Defense protects websites running PHP against zero-day attacks by blocking potentially malicious executions automatically and with zero latency.
If a user violates the security rules (trying to enter a wrong password, etc.), then Imunify360 will automatically block access to this user’s IP address, adding the IP address to the Gray List.
- Gray List – an auto-generated list of all the IPs blocked by the security software, based on Sensors alerts and alerts from the central server.
Imunify360 is available via accessing your
cPanel under the
Security tab:
From there, you will be greeted with the empty result menu, which is normal since no scans ran yet, as you can see below:
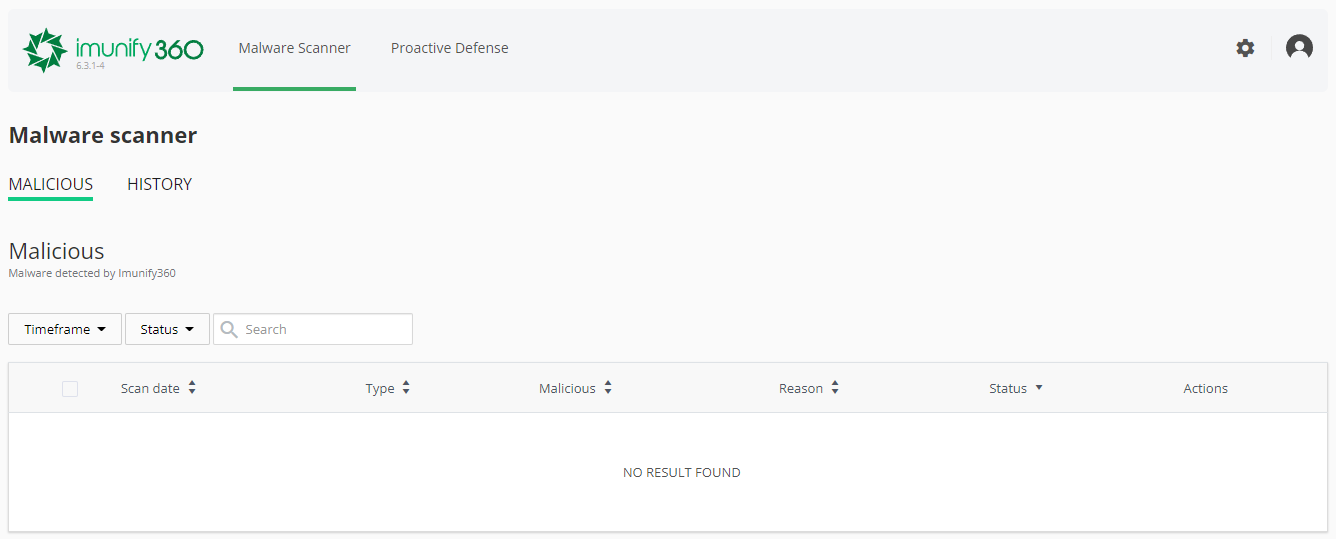
Imunify360 Malware Scanner
Malware scanning allows you to:
- Observe scanner activity;
- Start on-demand
- file scanner;
- Manage malicious and cleaned up files;
- Manage Ignore List.
From the button
Start scanning, you can prompt a user scan after a short confirmation:
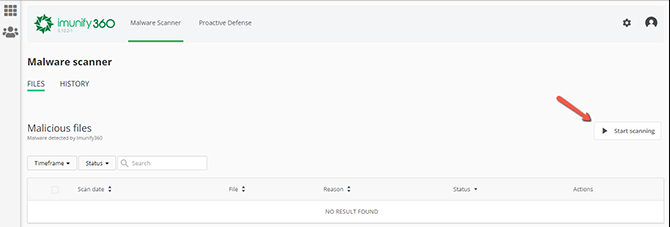
A scan will be scheduled. We advise you to wait for the scan to complete before making any changes to the files within your cPanel.
After the scan is complete, you will be prompted with either a malware-free cPanel:

Or the system will detect a present malware. Here is a table with a list of infected files within all domains.
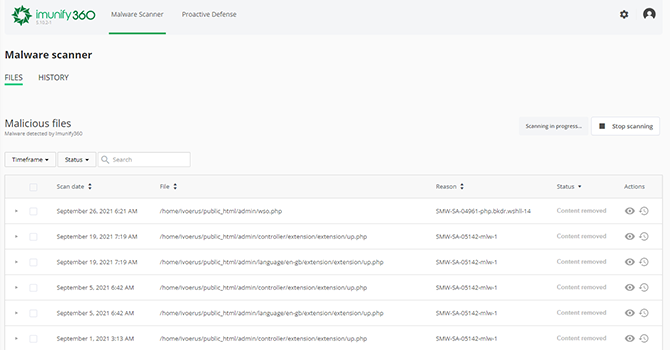
The table has the following columns:
- Scan date — Displays the exact time when a file was detected as malicious.
- File — The path where the file is located starting with root.
- Reason — Describes the signature which was detected during the scanning process.
- Status — Displays the file status:
- Infected — Threat was detected after scanning. If a file was not cleaned after cleanup, the info icon is displayed. Hover mouse over the info icon to display the reason.
- Cleaned — Infected file is cleaned up.
- Content removed — A file content was removed after cleanup.
- Cleanup in progress — Infected file cleanup is in progress now.
- Actions
- View file — Click the View File symbol
 in the file line, and the file content will be displayed in the pop-up. Only the first 100Kb of the file content will be shown in case if a file has a bigger size.
in the file line, and the file content will be displayed in the pop-up. Only the first 100Kb of the file content will be shown in case if a file has a bigger size. - Restore original file (before cleanup) — Click the Restore Original symbol
 to restore the original content removed as infected.
to restore the original content removed as infected. - Add to Ignore List — Add the file to the Ignore List and remove it from the Malicious files list. Note that if a file is added to the Ignore List, Imunify360 will no longer scan this file. Click the Gear symbol
 and select “Add to Ignore List.”
and select “Add to Ignore List.”
Imunify360 Proactive Defense
Moving on to the next tab,
Proactive Defense, which is a unique Imunify360 feature that can prevent malicious activity through PHP scripts. It is available as a PHP module for
Apache and
LiteSpeed web servers and analyzes script activity using known patterns like obfuscated command injection, malicious code planting, sending spam, SQL injection, etc.

Mode Settings
The following
Proactive Defense modes are available:
- Disabled — Means that the Proactive Defense feature is not working and the system is not protected enough.
- Log Only — Means that possible malicious activity is only logged, no actions are performed (default mode).
- Kill Mode — The highest level of protection — the script is terminated as soon as the malicious activity is detected.
To select a mode, you will have to contact our technical support department, which is
24/7 available, and will be more than happy to assist you!

The Detected Events table includes the following columns:
- Group/individual action checkbox — Allows performing actions on one or several desired entities.
- Detection Date/Time — Displays the date and the exact time of event detected. To view the exact time, click the clock icon in the desired event line. To order the events from the last to the first or vice versa, click the ▲ icon in the Date/Time of detection column header.
- Description — Displays a special Proactive Defense rule according to which a suspicious activity was detected.
- Script Path — Displays the path to the suspicious script. A number near the path describes how many times this event has been repeated.
- Host — Displays the host of the script.
- First script call from — Displays the IP in which the first call of the script was detected.
- White color means that this IP is whitelisted;
- Black color means that this IP is blacklisted;
- Gray color means that this IP is graylisted;
- All the other IPs are blue-colored.
- Action — Displays the current mode.
Imunify360 is part of every shared hosting plan and is included for no extra cost for you to use.